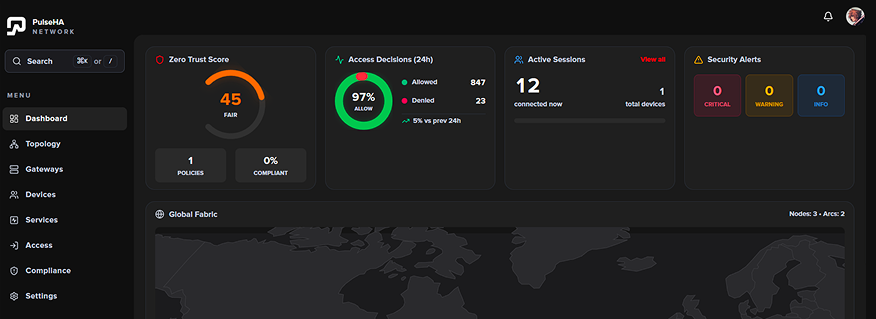
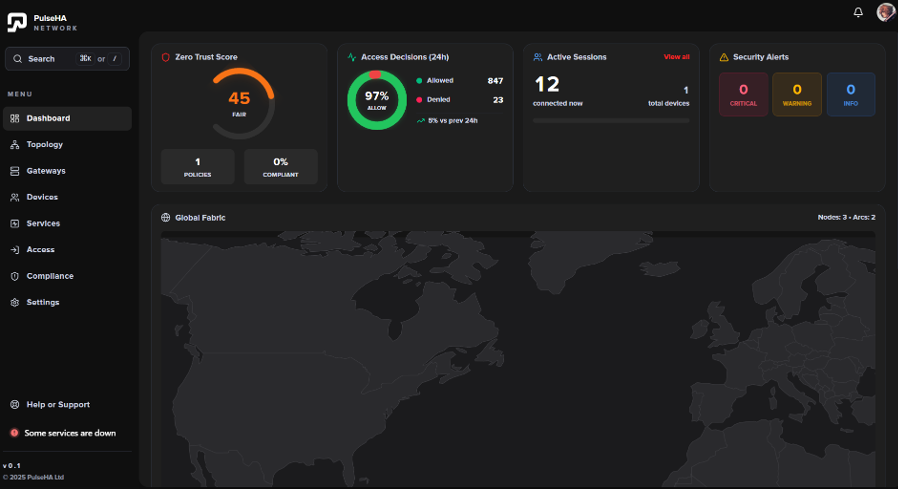
How It Works
The complete zero trust stack. One adaptive network.
See how agents, identity, policy, gateways, and services work together whilst continuously verifying access and adapting as conditions change.
Agents
Lightweight clients on user devices establish secure, encrypted connections and continuously feed device context into access decisions.
- Cross-platform support
- Automatic updates
- Device posture checks
Identity
Every connection starts with strong identity verification using your existing identity provider and is continuously re-evaluated as conditions change.
- Seamless SSO integration
- MFA enforcement
- Role-based access
Policy
Granular policies evaluate context including user, device, location, and time before granting access and continue to be enforced as conditions change.
- Context-aware rules
- Real-time evaluation
- Full audit logging
Gateways
Distributed gateways terminate connections at the edge and continuously route traffic to healthy backends as conditions change.
- Global distribution
- Continuous health monitoring
- Smart routing
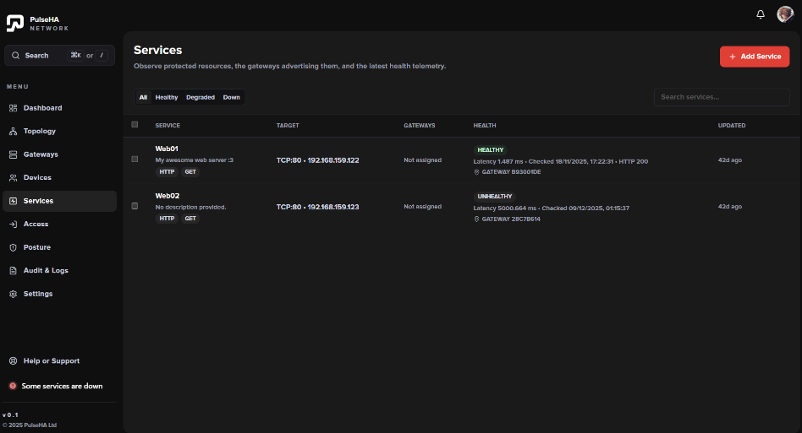
Services
Your applications remain invisible to the internet and are only reachable by authorized users through continuously enforced access controls.
- Zero exposure
- Application level access
- End-to-end encryption
One Adaptive Zero Trust System
See how all five components operate as a single system from the initial agent connection through to secure service access in real time.
- End-to-end flow
- Zero trust in action
- Complete security